Clean water is fundamental for every city. To ensure its purity, proper treatment is crucial to remove any contaminants. Equally important is the availability of accurate data to detect and address any potential issues.
SCADA's Role in Water Management
In the past, water districts relied on manual monitoring by employees who were hired to gather and record data in real-time. This hands-on approach was the standard for years, playing a crucial role in maintaining water infrastructure and quality standards.
Fortunately, advancements in technology have led to a new approach known as SCADA (Supervisory Control and Data Acquisition). SCADA is an automated system that enables water plant operators to control processes while receiving real-time data. Every city, regardless of size, depends on this system to ensure that water remains safe and uncontaminated.
However, with ever-evolving cyber threats, it’s crucial for organizations utilizing SCADA networks to routinely enhance their security measures. New regulations require municipalities to fortify their systems to not only ensure compliance but also resilience against potential cyber threats.
Ensuring the Security of SCADA Networks
Every business that works with SCADA systems is subject to SCADA security concerns. These threats can extend far beyond individual entities, affecting both the broader economy and local communities. Below are some security risks for SCADA networks:
- Hackers: These are individuals or groups with malicious intent to exploit weaknesses in your network to gain unauthorized access to your systems. If they gain access, they have the ability to manipulate controls, steal sensitive information, and even sabotage the system. For water and sewer systems, this means potentially releasing contaminated water, flooding, or other disruptions in service.
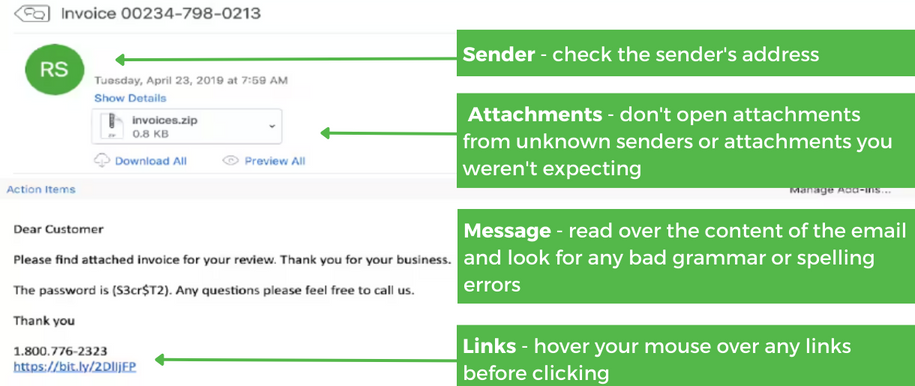
- Malware: Malicious software such as viruses, ransomware, or spyware can pose a risk to SCADA systems. To prevent phishing attacks, we recommend the SLAM method.
- Terrorists: In extreme cases, terrorist groups may target critical infrastructure such as water and sewer systems to create chaos, harm public health, or cause damage to the economy.
- Insider error: Not all threats to SCADA systems come from outside sources. Unfortunately, insider error can occur due to negligence, lack of proper training, and insufficient cyber security awareness. Inside error can lead to misconfigured controls, deleted data, or unauthorized changes leading to system failure or security breaches.
Without having necessary security procedures in place, managing SCADA networks can be challenging. Unfortunately, many networks remain vulnerable to cyber-attacks because they don’t have the right detection and monitoring systems in place. Further, SCADA systems can cost an organization from tens of thousands to millions of dollars, making them an attractive target. Because attacks to these systems exploit both cyber and physical vulnerabilities, it’s important to develop a comprehensive approach that integrates both cyber and physical security measures. To ensure robust security, it is important to implement a well-defined administrative structure and a clear hierarchy for enforcing security protocols.
It's Time to Schedule a SCADA Penetration Test
SCADA penetration testing is crucial for any organization that relies on SCADA systems to ensure the safety, reliability, and continuity of their operations. This type of test involves simulating real-world cyber attacks on SCADA systems to identify potential weaknesses, entry points, and other vulnerabilities. The primary objectives of the test are to:
- Detect vulnerabilities
- Assess security controls
- Mimic real-world attacks
- Test response capabilities
- Quantify risks
Working with Digicorp has proven to be a financial and operational win for our many customers. Let us help you! Fill out the form below and one of our representatives will be in touch with you shortly.